
There is not just the personal blog nowadays, perhaps a corporate blog which is written by executives and senior managers who have some level of authority in the company. They are the ones who are known to their customers and they are in a position to take decisions. They create the blog to promote their own company including the history or background information, their sales products and services and so on.
The definition of corporate blog is a blog published by, or with the support of, an organization to reach that organization's goals. There are five types of corporate blogs which are company blog (eg.Google, Adobe, Flickr, Facebook, and Yahoo! Search), CEO blog (eg.Sun CEO), industry blog, department or product blog (eg.Microsoft Community Blogs), and customer service blog.
Why blogs???
Firstly, you can become the expert, the position yourself and your company as the thought leader of your business. Secondly, blogs are fast way to join the customers' discussions, provide tips and insights or receive feedback, thus they improve the customer relationship.
Next, blogs are an easy way for the readers to find information and resources they want or need (blogging is on-the-job learning). Besides that, if you establish your company as a thought leader, people in your business will pay attention. They'll read and discuss what you have to say. Chances are good they will see you as an attractive employer.
The Advantages:
Corporate blogging can help your company feel more human to the world and it is a way for your company to become intertwined with the Internet community. In addtion, you could have thousands of people subscribing to your feeds if your corporate blog gains the popularity and this can equate to instant success and popularity of your products. 
Corporate Blogging: A new marketing communication tool for companies
Posted by Ah LiAn at 4:49 PM 1 comments
Review of Lelong.com.my
As the founders of the pioneer auction website (http://www.lelong.com.my) in Malaysia, Interbase has secured its position with the largest subscriber base for any site of this genre. With a mission statement of "Serving the community and bringing a high standard of quality into homes and businesses by providing an avenue for on-line trading at a low cost", the staff behind Malaysia's premier auction site continually strive to improve and develop its functionality without levying high costs. At present, Interbase is expanding into more areas of e-commerce and this review will allow you to better understand their business plan and vision.
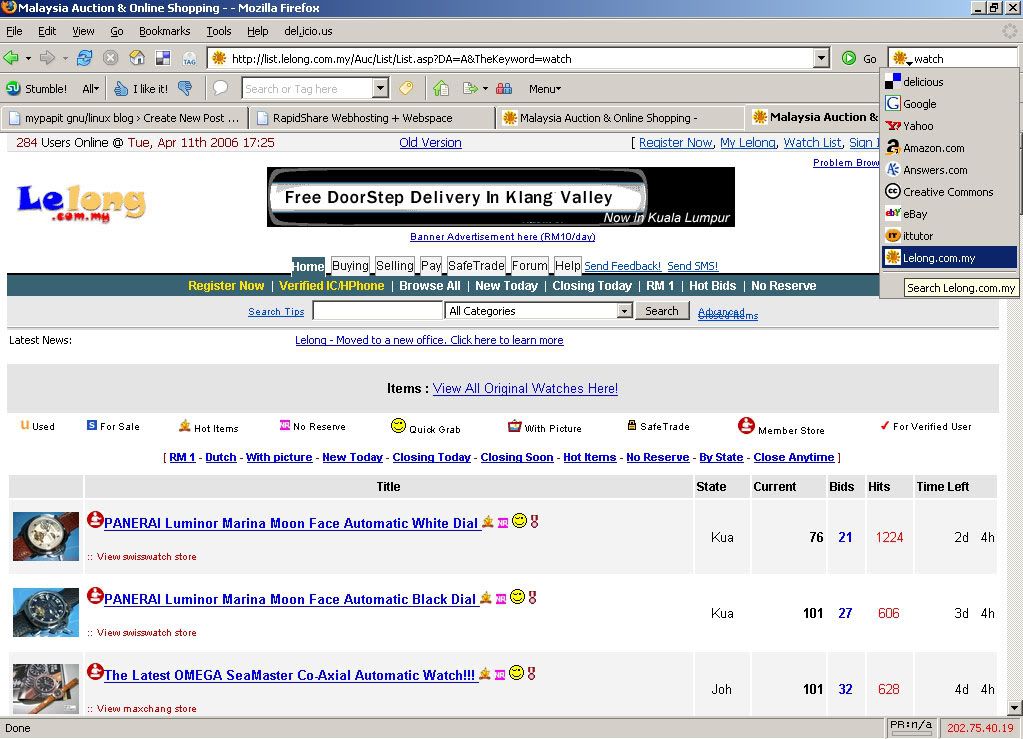
So what is Lelong.com.my? Styled and functioning similar to the international auction site, eBay.com, Lelong.com.my powers a robust and secure avenue for trading in Malaysia. The idea of an auction site in Malaysia has taken off with tremendous response. With a local flavour, members feel a sense of belonging and constantly keep in contact with the Lelong Development Team to give feedback, be it positive or negative. As their members are extremely valuable to them, they go to great lengths to accommodate for their needs and wants. With the experience they have gained from running the site for the past years, their team are well poised to deliver a site that is full of quality content to the members. Starting based on Consumer-to-Consumer (C2C) transactions, Lelong.com.my is now moving to becoming a channel for Business-to-Consumer (B2C) relationships. Many distributors have realised the power of using the auction system and are now using their site to trade and grow their business

What are the attractions of using Lelong.com.my? Many of us have lots of items lying around the house that are not currently in use; whether second hand or new items that we have not gotten around to disposing of. This is a major compelling factor that have brought many users to Lelong.com.my. The track record for selling items is extremely good. Approximately 70% of all items posted for auction on their site are sold. Hence, users stand a good chance of obtaining a successful transaction. The interface is very user-friendly and easy to use. At a glance, most users get the hang of the system. They focus heavily on customer support and in the event of any problems or queries arising, any e-mails / phone calls directed to them are responded to almost instantaneously. Problems that arise can also be posted in the forum and many users play a role in replyingout others. With all their on-going efforts, a community of auction users has formed which are extremely diverse, and who actively interact amongst one another. This causes them to feel at home and comfortable trading with other members.
Saturday, July 5, 2008
Posted by Joanne at 9:30 PM 1 comments
A review on a post on Legal from My E-Commerce blog
As part of its efforts to combat piracy and counterfeiting, Malaysia launched the Sikap Tulen campaign in July last year. It was an education Intellectual Property (IP) initiative targeted at relevant user groups. The aim of the Campaign is to cultivate a lifestyle that respects IP, and to encourage the behavior of using only original and licensed software. The strategy in Sikap Tulen Campaign is to integrate awareness, education and enforcement and execute tactics that focus at all levels ranging from companies, professionals, directors, IT resellers and society in general.
There are six components of the compaign which are as follows:
1. Sikap Tulen Profesional (Professional): a program to encourage professionals to adopt the right attitude towards respecting IP and rejecting software piracy.
2. Sikap Tulen Pengarah or Sikap Tulen Director: educating company directors to appreciate the importance of IP and to adopt the right practices in their companies.
3. Sikap Tulen Syarikat or Sikap Tulen Company: helping companies to implement policies that will help them take control of their software use.
4. Sikap Tulen Masyarakat or Sikap Tulen Society: nurturing a society that respects IP.
5. Sikap Tulen Mall IT or Sikap Tulen IT Mall: ensuring a piracy-free zone in IT Malls and IT stores in shopping complexes.
6. Ops Tulen: enforcement initiatives aimed at addressing the use of pirated and unlicensed software and enforcing the Copyright Act 1987.
Posted by sleeping beauty at 9:20 PM 0 comments
Things to take note to prevent e-auction fraud when a consumer participating in an e-auction
 (click to link to the webpage)
(click to link to the webpage)There are several types of e-auction fraud identified. Among them are:-
Bid shielding i.e. having phantom bidders bid at a very high price at the start of an auction and pull out at the last minute causing a bidder of a much lower price to win.
Shilling is by placing fake bids on auction items. The purpose here is to artificially jack up the bidding price.
Mighty Bids

(this website is currently unavailable)
Besides, e-auction fraud can also appear in a way whereby fake photos are taken and misleading descriptions given, improper grading techniques, selling reproductions as originals, failure to pay the auction house, high shipping costs and handling fees, failure to ship merchandise, loss and damage claims and others.
As such, it is important for users to know how to protect themselves from these frauds.The followings are several steps in protecting yourself against e-auction fraud:-
- User identity verification – a voluntary program that encourages users to supply eBay with information for online verification.
- Authentication service – a service to determine whether an item is genuine and described appropriately.
- Grading services – a service that determines the physical condition of an item.
- Feedback forum – a forum that provides users with the ability to comment on their auction experiences with other individuals.
- Insurance policy – investing in insurance policy that offers by the auction websites. For example, eBay offers insurance underwritten by Lloyd’s of London at no cost to eBay users.
eBay
 (click to link to eBay auction)
(click to link to eBay auction)Meanwhile, here are a few things buyers should take note of when participating in an e-auction.
Besides, buyers are adviced to check the seller’s reputation before purchase. Many auction sites have a section where every seller’s feedback score is displayed. Some sites even have a community-ranking system designed to every user’s profile so that buyers can always voice out their comments or feedbacks.
In addition to that, many sites provide buyer protection, for example courier delivery. Therefore, in cases where you don’t get what you pay for, you can always get a refund from the website.
On the other hand, buyers must also play their part in taking extra precautions and be smart in their purchase. For example, buyers must constantly bear in mind never to wire money to anyone’s account under any circumstances while paying. Instead, they should use one of the methods authorized by the website, such as paisa pay. Buyers must also read the rules of insurance before fishing out their credits. Most importantly, buyers must never give out their credit card numbers or any personal bank details via email.
Buyers also have to be careful as sometimes some sellers attempt to drive up the price of their own auctions by having several fake accounts. They can have multiple eBay identities that are all controlled by them, bidding on the same auction items you want neck to neck and it works especially when you start to get very involved with the auctions. Thus, buyer gets ego in the process of getting the product and foolhardily fell for the trick, causing him/herself to pay extra. In order to prevent this, buyer can check the seller’s auctions that have already closed and see if the same usernames are continually bidding (but never winning) in this auction.
On the other hand, if a buyer receive an email from a seller shortly after an auction closes stating that the winning bidder has defaulted and he or she is now the winner, chances are the seller is trying to scam not only one but many buyers. This is because; it takes several days for a bid to be defaulted. So if a buyer receives such emails within 3 days since the auction ended, beware!
Here is a link to some best auction websites

Monday, June 30, 2008
Posted by み莉 at 2:51 AM 0 comments
E-Government in Malaysia: Its implementation so far and citizen's adoption strategies
Electronic government was initiated with the initiation of Multimedia Super Corridor (MSC) by the Malaysian government in 1996.
In 1997, the Malaysian Government launched the Electronic Government initiative, generally known as e-Government. The purpose is to revamp itself to direct the country towards the Information Age. The implementation of e-Government in

E-Government seeks to enhance the convenience, accessibility and quality of interactions with the public and businesses at large. It will also improve information flow and processes within the government, its speed and quality of policy development, as well as the coordination and enforcement at the same time. Thus, this would enable the government to be more responsive to the needs of its citizens.

E-Government uses the information and communication technologies in public administration combined with organizational change and new skills to improve public services and democratic processes in order to strengthen support to public policies.

The seven main projects were identified to be the core of the e-government applications. The e-Government projects are Electronic Procurement (eP), Project Monitoring System (PMS), Electronic Services Deliverym (eServices), Human Resource Management Information System (HRMIS), Generic Office Environment (GOE), E-Syariah and Electronic Labour Exchange (ELX).
Other than these seven main projects under e-government flagships, several government agencies has also initiated online services for the public projects, aims to increase the ease and efficiency of public service to the people. Among others were Public Services Portal (myGovernment), e-Tanah, e-Consent, e-Filing, e-Local Government (e-PBT), e-Kehakiman, Custom Information System (SMK), Pensions Online Workflow Environment (POWER), and Training Information System (e-SILA).


E-Government is a way for public administration to become more open and transparent, and to reinforce democratic participation; more service-oriented, providing personalized and inclusive services to each citizen

Citizens today expect and demand governmental services with a high degree of quality, quantity, and availability in a 24-hour, seven-days-a-week, and year-round fashion. Governments all over the world are developing information systems and electronic services that have the capacity to meet these rising service needs and demands of citizens and other clients
The e-government applications are developed based on best understanding of citizen requirements. These applications will provide a seamless online service and thus improve traditional government services.
Despite the issue of privacy and security, internet security breakdown, the e-Government system will continue to grow due to the demand and the needs of the nation. It is the government’s strategy as the nation emerges towards our very own vision 2020.
Try this website to know more about e-Government services:

Posted by み莉 at 2:37 AM 0 comments
Mobile payment systems in Malaysia: Its potentials and consumers' adoption strategies

Mobile Money is a PIN-based Mobile Payment Solution designed by Mobile Money International Sdn Bhd to address the limitations and bottlenecks created by cash, cheques and credit cards. It allows registered users to pay for goods and services at anytime, anywhere using only a mobile phone coupled with a 6-digit security PIN (Personal Identification Number) via SMS (Short Messaging Service). This enables shoppers to buy products online and pay the merchant using their mobile phones without even being physically present at the store.
Mobile Money encourages more consumers to shop online. This will definitely be a great boon to the e-commerce industry in Malaysia. It also encourages more merchants to adopt online selling as an extra sales channel which complement perfectly with their offline sales channel to help them sell more of their goods and services.

Currently Mobile Money has teamed up with Hong Leong Bank Bhd and Bumiputra-Commerce Bank to allow consumers to make payments via their bank accounts linked to their mobile phones. It is targeting 1 million Malaysian mobile phone subscribers with the belief that sending cash via SMS will eventually become part of the daily life of the Malaysian community.
For latest information about Mobile Money, visit its website at http://www.mobile-money.com/Saturday, June 28, 2008
Posted by sleeping beauty at 11:22 PM 0 comments
Credit Card Debts: Causes and Prevention

Credit card is a system of payment named after the small plastic card issued to users of the system. In the case of credit cards, the issuer lends money to the consumer (or the user) to be paid later to the merchant. It allows the consumer to 'revolve' their balance, at the cost of having interest charged. However, it can lead to a big amount of debts or bankruptcy for the users or consumers.
The users might just keep on swapping the credit card unlimited because they don't have to pay the money on the spot. They didn't see where the money flows so they won't feel anything as long as they still have cash in their wallet. Some of them may hold 3 or 4 credit cards at the same time too. When there is due date, those users only pay the interest and the minimum amount of principal; they never fully pay for the amount. Finally, the poor money management and their self-attitudes will lead them to the pool of liabilities.

Besides that, the users might have to pay a big amount for medical expenses, deposits for buying cars or houses,thus they have to pay by using credit cards an owe money to the bank. Sometimes, the credit card debts may be caused by the internet threats such as phishing, malicious software, hacking and more. Due to the personal information, credit card number and the password have been stolen; the owners are liable for the bills which have been misused under their account.
The credit card owners should have a well-managed spending plan so that they won’t be wasting too much on unneccesary things and they can save money at the same time. Their attitudes have to be changed and they have to be self-disciplined too. In addition, credit cards should be cut up such as one person can only hold one card and the credit limit should be kept low. The credit card holders can learn the ways to detect the internet threats from security firms and report to them if they are being attacked.
Posted by Ah LiAn at 10:53 PM 0 comments
Electronic Currency
 Over the years, money as we know it has been evolving. The shape and form of money has changed from precious metals to metal coins and paper money with no intrinsic value and today we are presented with a formless form of money named digital or e-money. The digitization of money appears to be inevitable in the light of the recent developments with regards to the Internet and the various e-commerce opportunities presented by the world wide web. The future of e-commerce depends to a great extent on the appropriate development and diffusion of e-money.
Over the years, money as we know it has been evolving. The shape and form of money has changed from precious metals to metal coins and paper money with no intrinsic value and today we are presented with a formless form of money named digital or e-money. The digitization of money appears to be inevitable in the light of the recent developments with regards to the Internet and the various e-commerce opportunities presented by the world wide web. The future of e-commerce depends to a great extent on the appropriate development and diffusion of e-money.
Digital cash systems pose unique risks for both online merchants and consumers, including
 questions about security, the ability to safeguard users' privacy, susceptibility to counterfeiting, and suitability as a medium for online fraud. All of these generate fears among e-commerce merchants over increased legal liability. While traditional monetary systems combat fraud by using closed networks that block unauthorized access to the system, the open networks along which e-cash payments are transmitted often lack adequate safeguards against fraudulent access. Therefore, they must utilize elaborate encryption methods to code the information in such a way that only authorized parties can read it. New security apparatus and infrastructure must be devised to protect payment instruction transfers. A new public key infrastructure, which can be fairly expensive to implement but is required to diminish fraud risks.
questions about security, the ability to safeguard users' privacy, susceptibility to counterfeiting, and suitability as a medium for online fraud. All of these generate fears among e-commerce merchants over increased legal liability. While traditional monetary systems combat fraud by using closed networks that block unauthorized access to the system, the open networks along which e-cash payments are transmitted often lack adequate safeguards against fraudulent access. Therefore, they must utilize elaborate encryption methods to code the information in such a way that only authorized parties can read it. New security apparatus and infrastructure must be devised to protect payment instruction transfers. A new public key infrastructure, which can be fairly expensive to implement but is required to diminish fraud risks.Wednesday, June 25, 2008
Posted by Joanne at 8:08 AM 2 comments
A review on E-tailing
E-tailing refers to retailing conducted online, over the Internet. E-tailing makes it easier for a manufacturer to sell directly to the customer, cutting out the intermediary. The Amazon.com is an epitome of successful e-tailing business.
Amazon.com started as an on-line bookstore, but soon expanded its offerings to a variety of products and services such as media, electronics, toys, apparel and even groceries. Amazon reported over 1.3 million sellers who sold products through Amazon's worldwide web sites in 2007. Selling on Amazon has become more popular as Amazon expanded into a variety of categories beyond media, and built a variety of features to support volume selling.
The domain amazon.com attracted at least 615 million visitors annually by 2008 according to an Internet audience measurement website, Compete.com survey. In addition to that, Amazon attracts approximately 50 million U.S. consumers to its website on a monthly basis. This has proven how successful Amazon.com is conducting its e-tailing business!

“The logo that smiles from A to Z, revealing the personality of the worlds biggest online retailer.”
Click here to read more about e-tailing.
Tuesday, June 24, 2008
Posted by sleeping beauty at 11:47 PM 0 comments
The application of pre-paid cash card for consumers
A prepaid cash card allows consumers to purchase something even when they don’t have the cash to pay for it. It benefits consumers in their everyday life.
Though it works almost the same like a credit card, a prepaid cash card is different because it allows consumers to have a better control over their finance.
smooth operator
“Money shouldn’t slow you down. Life takes easy – with VISA~”
So, how does this work?
 click to link
click to linkAmBank NexG
 click to link
click to linkTune Money Sdn Bhd
 click to link
click to linkMaybank VISA
 click to link
click to linkA lot of people suffer from personal bankruptcy due to credit card debts. But a prepaid cash cards can change it all. The card is great for everyday purchases, special occasions, emergency back ups and etc. In short, it is safe, effective and convenient. Here is how it is…
The more famous Master card for
With so many credit cards being offered, consumer must bear in mind to get a card which best suits his/ her needs. Compare the different rates and features of all the offers available before making a decision is a wise thing to do.
Posted by み莉 at 4:02 PM 0 comments
The Application of 3rd Party Certification Program in Malaysia
Third parties are called certificate authorities (CAs), who issue digital certificate to provide verification that your website does indeed represent your company. One of the certificate authorities is MSC Trustgate.com Sdn Bhd. It is a licensed CA in Malaysia which incorporated in 1999, under the Digital Signature Act 1997 (DSA). It offers complete security solutions for individuals, organizations, government, and e-commerce service providers by digital certificates, encryption and decryption.
Besides that, VeriSign is the leading Secure Sockets Layer (SSL) Certificate Authority which also enabling the security of e-commerce, communications, and interactions for Web sites, intranets, and extranets. It provides security solutions to protect an organization’s consumers, brand, Web site, and network.
Why is the 3rd party certification needed? The reason is there are threats of internet security spreading over the net nowadays. For example, with the increase of phishing on the internet; customers want to make sure that whether they are dealing business with a trusted party. They are afraid of their personal information such as ID number, passwords, credit card numbers and so on, will be sent to those companies which do not exist in this real world. Thus, the certification from 3rd party is needed to ensure their information traveled over the Internet reaches the intended recipients and is safe.
Besides that, those parties are needed because they can provide e-mail protection and validation, secure online shopping carts and more services in order to avoid being spammed, hacked and attacked by the macilious software such as virus, trojan horse and worms.
Lastly, by applying 3rd party certification, there are more safeguard for online shopping, which means the customers can shop safely. In addition, the confidentiallity of customers towards the internet will also be enhanced and hence the organizations will be able to earn more profits.
Sunday, June 22, 2008
Posted by Ah LiAn at 2:58 PM 0 comments
How to safeguard our personal and financial data?
 Today, most people rely on computers especially the Internet to create, store and manage critical information. Information transmitted over the Internet is more vulnerable and has a higher degree of security risk than internal networks because they are open to anyone.Therefore, it is important that users take measure to protect their data from loss, damage and misuse.
Today, most people rely on computers especially the Internet to create, store and manage critical information. Information transmitted over the Internet is more vulnerable and has a higher degree of security risk than internal networks because they are open to anyone.Therefore, it is important that users take measure to protect their data from loss, damage and misuse.Safeguards against unauthorized access and use
Usernames and passwords are used to ensure security. Longer passwords provide greater security than shorter ones. Once you select a password, change it frequently. Do not disclose it to anyone.You should also be careful about where you save your password on your computer. Some dialog boxes, such as those for remote access and other telephone connections, present an option to save or remember your password. Do not select that option.



Other measures that safeguard against unauthorized access and use include firewalls and intrusion detection software. Users can use firewalls to protect their computers and data from unauthorized intrusions. Personal firewall utilities constantly monitor all transmissions to and from the computer and inform the users of any attempted intrusion.
Safeguards against information theft
 To protect information on the Internet and networks, individuals may use a variety of encryption techniques to keep data secure and private. Encryption is a process of converting readable data into unreadable characters to prevent unauthorized access.
To protect information on the Internet and networks, individuals may use a variety of encryption techniques to keep data secure and private. Encryption is a process of converting readable data into unreadable characters to prevent unauthorized access.
Posted by sleeping beauty at 1:02 PM 0 comments
EXAMPLE OF ECOMMERCE SUCCESS AND ITS CAUSES
As more organizations began to start their own online operations the company that helped get it all started was in danger of seeing its market share eroded by the competitors it helped created. Amazon has nearly 49 million active customers. Last year itself, they bought more electronics holiday related items than books, a first for the company.
With $6.92 billion in sales in 2004, Amazon ranked at the top of Internet Retailer's annual top 400 list, well ahead of computer maker Dell Inc., which posted $3.25 billion in online business-to-consumer sales. Office Depot Inc., which has a partnership with Amazon, wasn't far behind with $3.1 billion.
The reason why Amazon is so successful is because they had slowly built up their market brand and trust in their products. This tactic keeps the customers coming back for more an it attracts new clients to come. Other than that, they force their technological developers to focus on value delivered to the customer instead of building technology first and then figuring how to use it.
Amazon also takes it granted stuff you cant win everything, that’s reality, embrace it. For example, go more with a fast reboot and fast recover approach. With a decent spread of data and services you might get close to 100%. So what do they do? They create self-healing, self-organizing lights out operations.
Amazon also believes that the only way to manage as large distributed system like theirs is to keep things as simple as possible. Keep things simple by making sure there are no hidden requirements and hidden dependencies in the design. Cut technology to the minimum needed and only those that are needed to you need to solve the problem you have. It doesn’t help them to create artificial and unneeded layers of complexity.
Besides, Amazon.com also stresses on the importance of innovation. Amazon.com believes that everyone must be able to experiment, learn, and iterate. Position, obedience, and tradition should hold no power or innovation will never boom.
Wednesday, June 18, 2008
Posted by Joanne at 10:25 PM 0 comments
Phishing: Examples and its prevention methods.
Phishing is somewhat like fishing. The way you do it is almost the same but the tools you use are different. Phishing is an e-mail scam. The phishers puts the bait to fool and lure innocent prey and steal their identity before they know it. Victims will receive justifiable-looking emails which look as if they are from valid company websites.
These emails will take them to a phony scam site and requires them to login to their account and key in some private details of their own like bank PIN number, credit card number, passwords, account data, other personal information and etc. Or, it can also be a pop-up window which looks exactly like the official website.
With the information, the perpetrator will then conduct bank and credit card fraud. This is the most outraging daylight robbery of identity of the new century. Websites that is often spoofed or mocked by phishers are eBay, MSN, Yahoo, America Online (AOL) and PayPal.
The following are the examples of phishing scams.
eBay E-mail
 According to the email (as shown above), a slight billing error have occurred due to the reasons given. As such, the victim was told to login and verify the transactions. The logo of eBay used here is a real one. However, this is easy because such logos can be obtained from the real site without any hassles. It is also one of the ordinary approached employed to lure the victim.
According to the email (as shown above), a slight billing error have occurred due to the reasons given. As such, the victim was told to login and verify the transactions. The logo of eBay used here is a real one. However, this is easy because such logos can be obtained from the real site without any hassles. It is also one of the ordinary approached employed to lure the victim.Citibank Scam

The warning letter instructed the customer to renew his records by keying in some sensitive financial data so that the company could secure and protect the safety and the integrity of the customer. Little did the customer know if he or she ever adheres to such instructions, it will be the end of the safety and the integrity of his/ her account as mentioned.
Here is how and what you should do in preventing yourself getting phished.
There was this Chinese saying that goes like: if you know yourself and your enemy well, you are sure to win the game.
Phishers normally wants their victims to react on the double; otherwise, their tricks will fail. So, they will include some exciting or warning signs to spark your alarm. For example, they can deceptively claim that there is some error in processing some transactions in your account or some unusual withdrawals have been made, thus you are required to logon to a scam site in order to verify it. They can also make a deceptive claim saying that you were chosen to be the winner of a lottery ticket and thus you have to enter some personal information before you can receive your mysterious gift.
If this is so, users should check and report the incident to the actual financial institution or company that is supposed to have sent you the mail. Confirm the incident with them before submitting yourself to the scam. This could help the banks and companies to take actions against preventing fraud too.
2. Be wary of impersonal emails.
Most of the time, perpetrators attack millions through spam mails; which means to say, a phish mail is by large, impersonal and general. This is in contradictory to true emails from financial institutions as they are mostly personal in nature.
3. Never give away your personal financial information by filling up forms that comes in emails.
A predictable phishing scam normally requires victims to enter their personal information like usernames, passwords, credit card numbers, bank account PIN number , Identity Card number (for the Malaysian context) via an online form. This is quite the opposite of a true valid financial institution. Because a bank would normally have good control over customers’ account and will not ask for such information. Otherwise, my advice to you is better transferring your money to another safer and more responsible bank.
Log on to http://www.anti-phishing.info/avoid-phishing.html for more tips in preventing getting phished.
So, the moral of the story is: be extra careful in giving away your personal information. Report such scams if you ever come across one. You never know, you could make an impact in someone else’s life! =)
Posted by み莉 at 9:05 PM 0 comments
The threat of online security: How safe is our data?

and those caused by intentional misrepresentation. Misrepresentation is most often leds to online fraud and identity theft. Malicious code, on the other hand, is at the root of so-called "crackings" and "hackings" are the most notable examples of which include computer viruses, data theft, and Denial of Service (DOS) attacks.
So what can you go to help protect yourself against these threats?
(1) Buy and install a good anti-virus application on your PC. This software protects against viruses and malicious code that arrive through email and other methods. The most critical element in using anti-virus software is to make sure the program is regularly updated with the most recent virus definitions. These are patches that allow the software to identify and tackle the newest viruses. Good anti-virus software will automatically update itself on a regular basis.
(2) To protect against intruders, computer users can also install a personal firewall, which blocks unauthorized attempts to gain access to a computer, and even makes a computer "invisible" to hackers scanning the Internet for potential targets.
(3) Choose your computer passwords wisely
(4) Disable file and printer sharing on your computer
(5) Keep security and system patches up to date
For more information you can visit this site:http://www.entrepreneur.com/technology/techtrendscolumnistpeteralexander/article78616.html
Posted by Joanne at 9:02 AM 0 comments
A Review on Internet Security
Internet has been developed for at least ten years and it definitely provides a lot of benefits to users such as, saving time and costs especially in E-commerce areas. Nevertheless, every thing in this world has both sides of good and bad. It can bring you happiness but also the worries and suffers.
There are some deficiencies by using Internet. The possibility of its risk exposure is high and it will cause a lot of problems to all fields of users especially those who are dealing business by Internet. What are those deficiencies or issues of the internet that are so important to make people be so alert? What are the effects of lacking of Internet security? Will the effect cause a big amount of losses to users?
People are concerning about the internet security problem and this is the main issue that the whole world should focus on. Malicious software programs are increased with a high rate as compared to previous time. Computer viruses, worms, and Trojan horse are the threats of malware. They could destroy the programs and data as well as disrupt or even halt your computer networks operation. You can imagine that if your Pc has been disrupted, your whole entire files and data like those assignments could have been destroyed. You will be crazy definitely. So, what about those big companies and organizations? How much of losses that they could bear if that happen to them?
Besides that, spyware will install itself to your computer secretly and monitoring your web surfing activities, and even offering outsiders the possibility of stealing your personal identity and information. Due to this reason, there are people always report that their credit card numbers have been stolen and this makes them used to pay for the bills that are not consuming by them but under their account. If this happen to those who are doing online businesses, you can imagine that how broke they would be. Thus, there are still some people do not perform online transactions such as buying from net, because they are afraid of their privacy would be invading.
Definitely, the problem is dealing with the unsecured data. Some organizations are found that they are not doing enough to secure their data and it is dangerous of losing of sensitive data. When we register or sign up for email, forum, blog and others, there are personal information required such as name, date of birth, and password. We do not know that whether our private information are secured or they would be sold for others by the organizations.
Even though you have conducted plenty of preventions such as install anti-virus software, avoid using one password for all accounts that you create, and other security packages, we are still exposed to the risks because those cyber criminal groups keep on creating new tactics to hack in your computer system, spam your email as well as tapping Wi-Fi from the neighbourhood. @_@
Fortunately, International Multinational Partnership Against Cyber Terrorism (IMPACT) which has the best brains and facilities, being set up to help fight the cyber security threats. In addition, the corporation such as Symantec Corporation, TrendMicro and F-Secure will also be the partner of IMPACT to assist us how to defense against the cyber criminal. Although the internet security problems are increasing, we still have to access Internet because it is an important tool in our life. There are the responsibilities of all users to protect the data and information. All users should provide enough to secure and protect themselves regardless small companies, large organizations or personnel.
In a nutshell, I hope that internet security can be more improved and provide more integrity for users so that they can access it safely, trustily, and happily. Computers, software, programs, virus etc, all are created by human, all are human being. In this world, if a human could come out with one thing, another would also be able to contrast it. If the cyber criminal groups come out with new tactics, there would be someone can fight against it. ^^
Tuesday, June 17, 2008
Posted by Ah LiAn at 11:27 PM 0 comments
An example of an E-Commerce failure and its causes
 Webvan was one of the most epic fails in the dotcom bubble fiasco. The online grocer was founded in 1999 by Louis Borders and was headquartered in Foster City, California, USA. Webvan delivered products to customers' homes within a 30-minute window of their choosing. It served customers in ten US markets: Chicago, Los Angeles, San Francisco Bay Area, Orange County, San Diego, Seattle, Portland, Dallas, Atlanta and Sacramento.
Webvan was one of the most epic fails in the dotcom bubble fiasco. The online grocer was founded in 1999 by Louis Borders and was headquartered in Foster City, California, USA. Webvan delivered products to customers' homes within a 30-minute window of their choosing. It served customers in ten US markets: Chicago, Los Angeles, San Francisco Bay Area, Orange County, San Diego, Seattle, Portland, Dallas, Atlanta and Sacramento.Many analysts have said Webvan spread itself to too many locations too quickly. The enormous infrastructure that Webvan thought to establish in multiple geographic areas has proved to be too great a cost. Besides that, Webvan faced a number of challenges in its short existence, including a sharp economic downturn, sluggish consumer spending and investor indifference.
One of the hallmarks of the dot-com crush has been the presumption that you needed to get big fast. It has been proven in Webvan's case which made the company a relic of the dot-com flops. A core lesson from the dot-com boom is that even if you have a good idea, it's best not to grow too fast too soon. (see cnet.com)

This site exists now as merely a traditional link farm.
Saturday, June 14, 2008
Posted by sleeping beauty at 4:53 PM 0 comments
The history and evolution of E-Commerce
Do you guys still remember that we lined up for at least half an hour, to buy the stupid movie ticket in previous time? It’s irritating, isn’t it? But nowadays, internet has changed the way that we buy and sell goods or services. Most of us make business transactions online on such a regular basis such as online-booking for the movie ticket and airline ticket as well. Therefore, this activity or action of buying or selling of goods and services over the internet is called “E-Commerce”.
So, how did E-Commerce get started? Well, let me explain to all of you here. In 1960s, those companies and businesses were using ancient computer networks to carry out the electronic transactions. Electronic Data Interchange (EDI) had been introduced to help the companies for interfacing and trading without human conduct such as sharing business documents invoices, order forms and shipping confirmation with another company's computer.
Until 1979, the American National Standards Institutes (ANSI) had come out with ASC X12, which is a universal standard for sharing business documents over the electronic networks. It is adopted to standardize the EDI to assist the businesses would be able to complete the electronic transactions with one another reliably. After 15 years, the Mosaic web-browser or Netscape was made, people had their first time to buy things off their computer. Mosaic browser was quickly adapted into a downloadable browser, and for Netscape, it is allowed easier access to e-commerce.
In 1998, people came out with Digital Subscriber Line (DSL) and cable connections, which provide fast, always-on Internet service to subscribers. It allows a computer to stay connected all the time and prompts people to spend more time, and money to online. Thus, E-commerce becomes more popular. The largest bookstore, Amazon.com and the electronic paying field which is eBay are the two companies that transformed e-commerce in 1990s.
Unfortunately, at the turn of the twenty first century, the dot-com bust happened and many of these businesses went broke because of many people still didn’t have high speed Internet in their homes and many small businesses were lacking of funds to create the web sites. However, it does not stop people from using e-commerce.
In 2000s, those booming trading online, travelling with tickets purchased at discounts over the Internet have lead to e-commerce accounting for 1/3 of the total economic growth of its. Today, those average persons have the high speed Internet connection that lets them move easily between web pages. This makes it easy to do comparison-shopping online. More importantly, it has increased the ability of people to work from home to set up e-commerce sites also.
In conclusion, E-Commerce is still one of the leading forces of economic growth today. People are now familiar to buying tickets over the Internet and shopping for gifts. It can bring a lot of benefits to users, suppliers and customers such as saving time and costs. It may also have some technological limitations or nontechnological limitations such as security and privacy, lack of trust and etc. But, with the Internet still in its infancy, the future of e-commerce has the ability to change and again revolutionize the way people think about shopping
Tuesday, June 10, 2008
Posted by Ah LiAn at 10:44 PM 0 comments
Discuss how E-Commerce can reduce cycle time, improve employee empowerment and facilitate customer support.
Cycle time is the period of time required to complete a process, function or operation from start to finish. Business-to-business (B2B) E-Commerce helps company to increase their efficiencies and effectiveness by reducing the transaction costs. For example, a customer from
Meanwhile, empowerment aims at granting employees the authority and the responsibility so as to act in response to customer requests within a short time. Nowadays, no one can survive in the business world without having any IT knowledge. People now look forward to complete their tasks using the shortest time possible and with E-Commerce, such objective can be achieved at anytime. For example, employees now can work from home and cut down on traveling because traveling not only takes up a lot of time, but is also costly as well. Besides, in some companies, customer complaints are handled online. Feedbacks from the customers are recognized as to be important to the company’s growth and development. Therefore, some companies actually collect and respond to customer complaints online as it saves time and is very convenient now. I remembered last Christmas; I was shopping with my sister at Giordano, Mid Valley. I wanted a shirt very much but my size ran out of stock at that time. One of the sales girls, not wanting to disappoint me, offered to help to ask if other branches have my size. It just so happen that the Giordano at One Utama has the stock and the sales girl booked aside for me so that I could collect it from Giordano at One Utama later. The point here is, the Giordano branches are all linked together. They share effort in pleasing their customers by empowering their staffs to do so.
E-Commerce facilitates customer support by reducing inventory and overhead costs. With that, the “pull-type” supply chain management is implemented which integrates also the just-in-time (JIT) system. The “pull-type” processing system is a competitive advantage to the companies as customer gets to tailor their products and services according to their preferences. This is widely practice in Dell Computer Corporation.
Besides, shopping today is made easy with E-Commerce. Shoppers online are provided with more choices than ever. With E-Commerce, shoppers can get information they need in seconds and compare prices before purchasing. In a way, E-Commerce assists in providing competitions between suppliers. Transactions are also made easy as it enables customers to trade at any hour of the day. But then again, there are disadvantages for shopping online too. You see, there was this once when my friend and I bought some bags online. It was a Taiwanese website which I have lost the URL. The stocks came later than as promised and it turned out that some of the bags are dirty.
E-Commerce has made life easy somehow; it has its own disadvantages at the same time.
Posted by み莉 at 12:19 AM 0 comments









